Cybersecurity is a growing concern for organisations all over the world, especially since they are accumulating more and more technology in their gradually expanding IT networks. And to make things even worse, cybercriminals and hackers are getting smarter and more sophisticated all the time. This has a lot to do with the power of automation, which makes it easier for them to carry out large-scale attacks on various random and carefully sought-out targets.
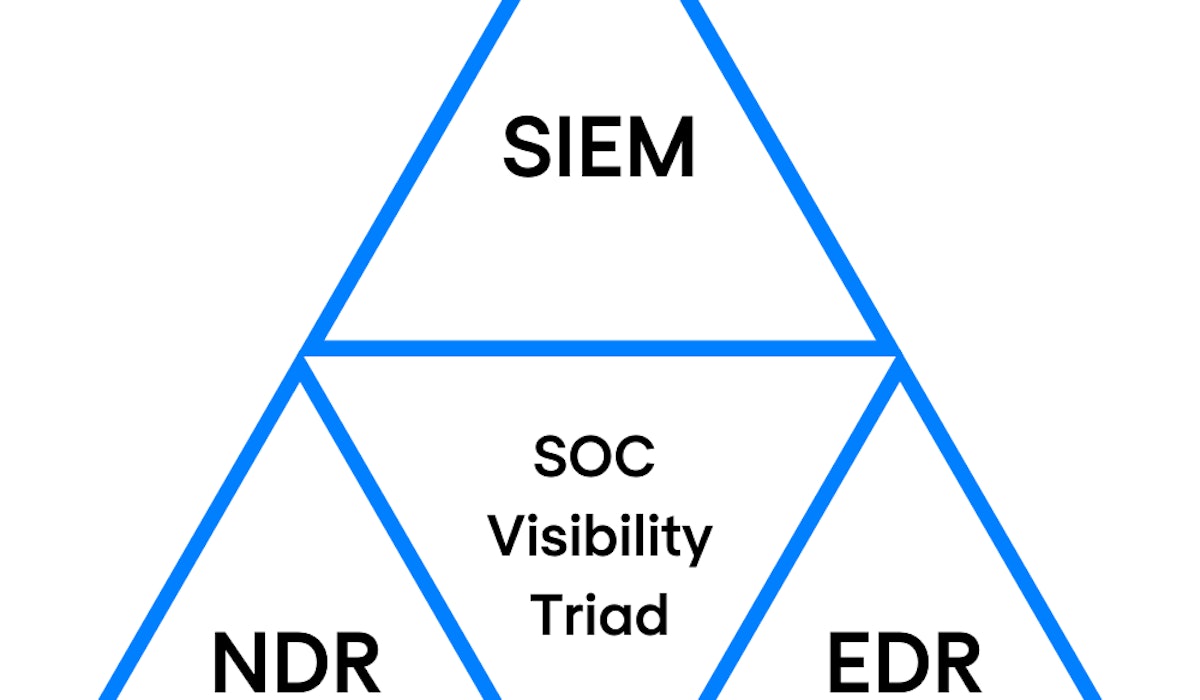
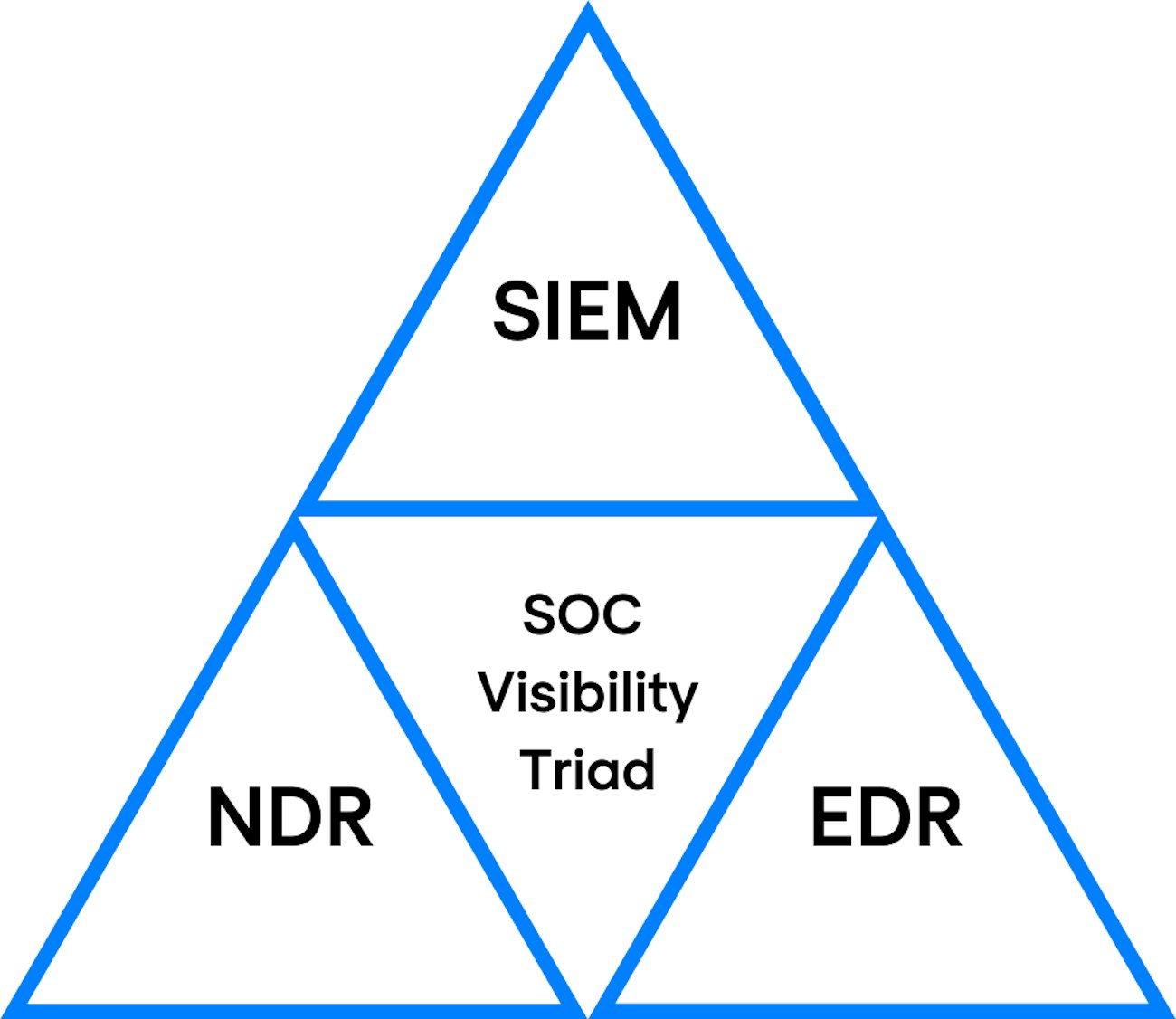
The main challenge for the security teams facing the daunting task of keeping modern cyber attackers at bay? Getting the necessary visibility in every corner of increasingly complex IT environments. To make this task easier, Gartner introduced the network-centric concept of the SOC visibility triad. What does this concept entail? And what are the main benefits of the SOC visibility triad? In this article, we will provide you with the answers to these pressing questions.
Three core elements of the SOC visibility triad
As the name suggests, the SOC visibility triad relies on three well-known core security elements.
- User and entity behaviour through security information and event management, a security strategy that is better known as SIEM.
- Network detection and response (NDR).
- Endpoint detection and response (EDR).
Let’s take a closer look at each of these security pillars and find out how they complement and strengthen each other.
SIEM
SIEM has its strengths and benefits, but it also has a couple of weaknesses when it comes to dealing with advanced security threats. The method mainly relies on logging mechanisms to detect threats and vulnerabilities. The problem is that certain system exploits and vulnerabilities don’t or rarely show up in logs. Also, certain technologies and systems don’t allow or support log collection.
Although a modern SIEM solution is a good tool to provide a first line of network defence, it should be complemented by an extra security layer. Every SIEM is only as powerful as its data source. Without reliable feeds and sufficient coverage, the SIEM is as good as blind.
NDR
And that’s where NDR enters the modern security equation. NDR complements the log analysis that a SIEM solution performs. It does this by correlating detected threats with network activity, thus covering for (possible) logging gaps. NDR provides the important network data that the SIEM needs to add context to the various threats and vulnerabilities that it detects.
The combination of modern-age SIEM and NDR technology allows you to utilise data from a wider array of sources. The result? Better network visibility, more thorough analytics and the ability to respond quicker to potential threats and security breaches. NDR helps you to increase the scope of protection provided by a stand-alone SIEM solution.
EDR
The third component of the SOC visibility triad is endpoint detection and response (EDR). EDR is a predominantly behaviour-oriented security technology that focuses on the detection of malicious activity that occurs directly on an endpoint (server, desktop, laptop). The significance of EDR in combination with SIEM and NDR? It gives you the opportunity to recognise the signs of an attack in the earliest possible stages. Subsequently, your cybersecurity team can remotely isolate the host from the network for further investigation in such a way that only the analyst has access to that specific machine.
Three beats one
But what makes the SOC visibility triad such a strong and useful weapon in the ongoing arms race between cybercriminals and security professionals? Its main advantage is that the solution harnesses the strengths and mitigates the weaknesses of the separate security solutions that build the triad.
We can illustrate this with a couple of examples.
- The sheer amount of data that you have to analyse is a complication that comes with NDR territory. Adding SIEM and EDR to the mix enables security analysts to redefine NDR in situations where network visibility is a concern. End-to-end encrypted network connections are a good example.
- NDR also complements EDR by closing EDR agent gaps (EDR depends on agents to carry out monitoring processes, but these agents are not always available). The main benefit of this strong EDR-NDR combo? It becomes a lot easier to detect malware that tries to evade EDR monitoring.
On their own, each of the three components of the SOC visibility triad have their unique strengths and weaknesses. The value of the SOC visibility triad lies in the fact that the solution allows each component to augment the others, maximising the strengths and minimising the weaknesses. Thus, the SOC visibility triad creates strength through diversity and offers a multi-layered and holistic approach to network security that sends a clear signal to cyber attackers: get out and stay out!
Understanding the basics of cybersecurity
Get your copy of this 70+ pages whitepaper, to learn more about cybersecurity and to feel comfortable in a security conversation. Or get in touch with us directly if you find this topic of interest.

Updates

Phishing Cybersecurity
A custom app to decode QR codes in phishing emails
Cybercriminals frequently use emails as their main method for phishing, embedding dangerous links or QR codes. To face this problem our SOC analysts have created a special app designed to tackle the issue of QR codes in phishing emails.

Lydia Pieternella

SIEM
8 factors you should consider before implementing SIEM
Implementing a SIEM system involves key steps like defining objectives, ensuring compatibility, calculating costs, assessing skills, ensuring compliance, evaluating infrastructure, selecting a reliable vendor, and future-proofing for cybersecurity.

Cybersecurity
Secure your future: Top cybersecurity trends for 2024
We’re on the brink of a new year again. Time to learn all about the most important and interesting cybersecurity trends for 2024.

Mohamed El Haddouchi