Security Information and Event Management (SIEM)
In today's interconnected world, businesses face an ever-evolving landscape of cybersecurity threats. From ransomware attacks to insider threats, the complexity and volume of these challenges can be overwhelming. Enter Security Information and Event Management, or SIEM—an essential technology that empowers organisations to have a more unified and comprehensive view of their security landscape.
SIEM systems act as the centralised hub for collecting and analysing data from a wide range of sources within an organisational network, including servers, firewalls, antivirus programs, and other security software. By consolidating this information, SIEM solutions provide real-time analysis of security alerts and events, facilitating quicker identification, assessment, and remediation of potential security threats.
Why Nomios
Nomios is pivotal for organisations seeking to implement a SIEM solution. We offer technical experience and industry insights that facilitate seamless integration and management of advanced SIEM solutions. Collaborating with a diverse partner ecosystem, we align innovative technology with organisational objectives, refining network architecture and boosting security frameworks.
We provide strategic counsel, extensive post-implementation support, and promote knowledge transition to internal IT teams, equipping them with the skills to manage and modify the SIEM solution adeptly. Our unbiased, expert advice helps organisations select the most appropriate solutions, irrespective of the vendor, aligning precisely with strategic needs and goals.
Choosing Nomios for your SIEM solutions ensures that your organisations will acquire knowledgeable, strategic, and unbiased counsel, enabling secure, considered solutions to improve operational efficiency and fortify security across your network landscape.
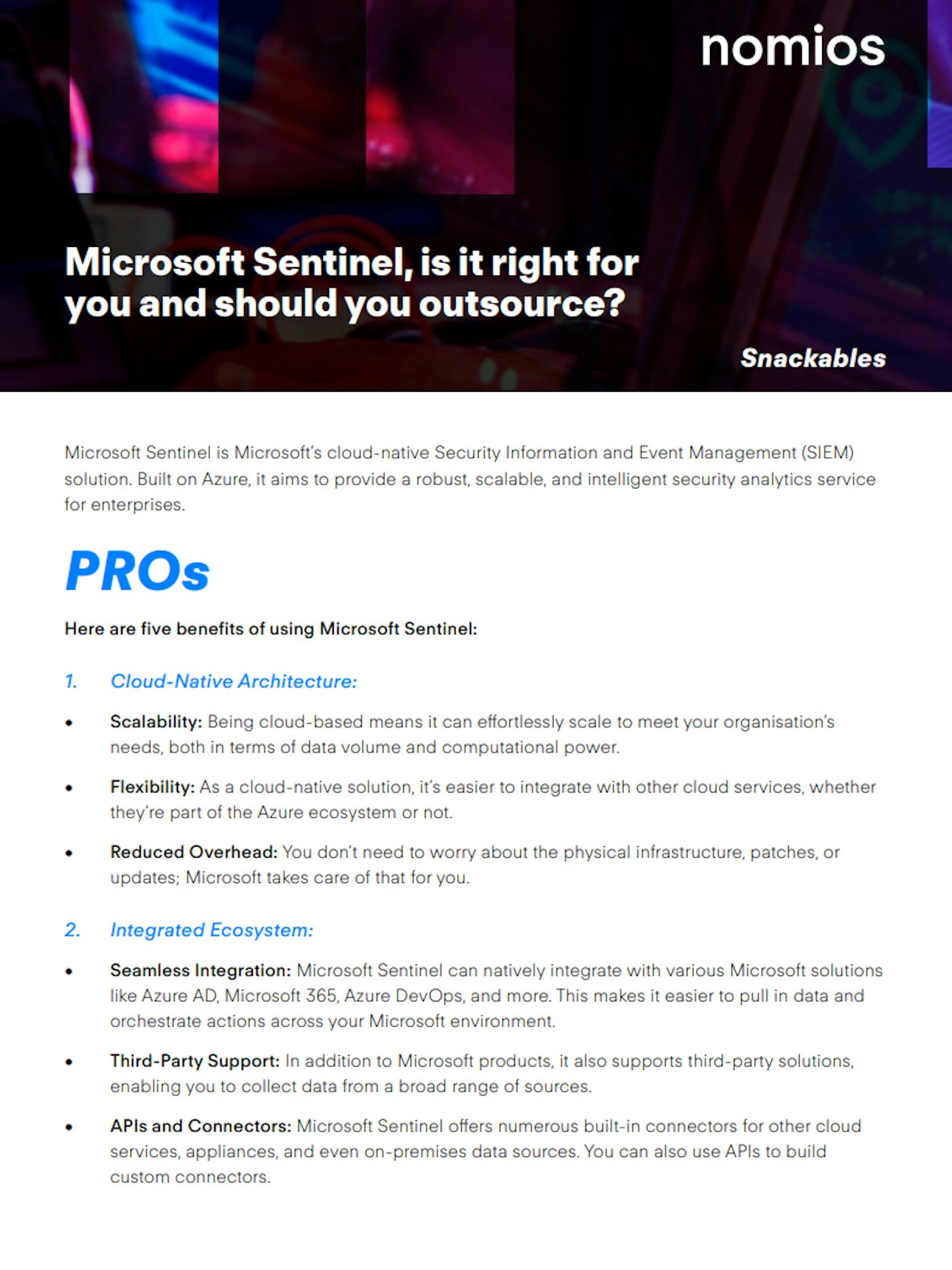
Unleash the Power of Next-Gen SIEM
SIEM offers these features as a proactive and reactive measure to bolster an organisation's cybersecurity framework. Whether you are a small business seeking to safeguard customer data or a large enterprise aiming to protect complex infrastructures, a SIEM system can offer invaluable insights and controls to enhance your security posture.
Log aggregation
- Collects and consolidates log data generated throughout the organisation's technology infrastructure, from host systems and applications to network and security devices.
Real-time monitoring & dashboard
- Analyses data and activities in real-time to pinpoint abnormal patterns or signs of potential threats, while summarising the security status of an organisation's network, offering a clear view of key metrics and ongoing activities.
Alerting
- Notifies system admin of potential security incidents by flagging events based on severity, frequency, or other predetermined conditions.
Incident response
- Automates and assists in the process of addressing and resolving security incidents.
Event correlation
- Links related records and identifies patterns that might indicate a security threat.
Compliance reporting
- Helps organisations adhere to industry regulations by generating compliance reports, which can be crucial for legal and auditing purposes.
Talk with our cybersecurity experts today
Our European cybersecurity experts are available now for a call or video meeting. Let's talk about your network challenges, discuss solution suitability, or talk about vendor solutions or upcoming network projects. We are here to help.

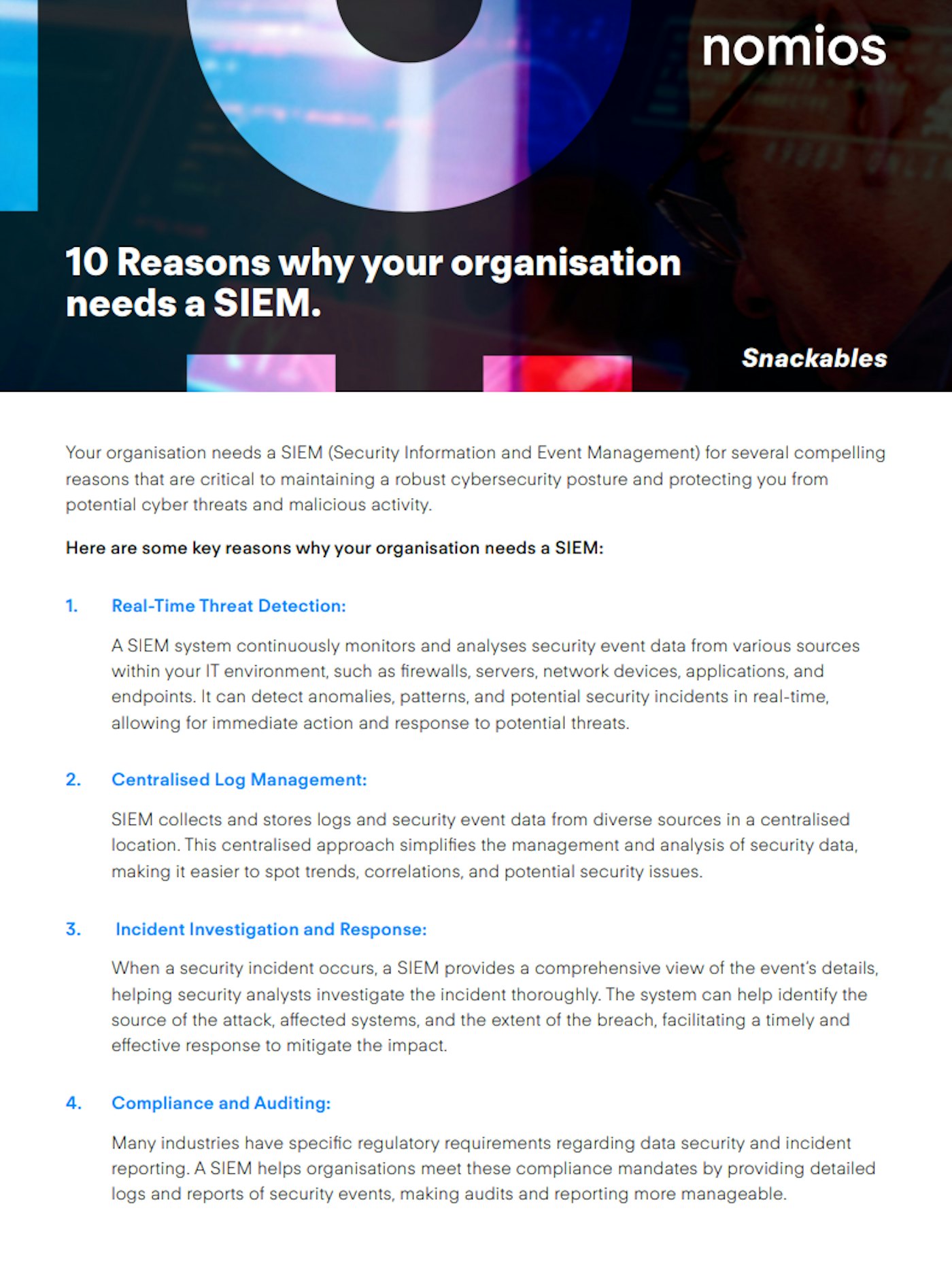
Reasons why to use SIEM
The adoption of SIEM technology offers a multitude of benefits, each serving to improve an organisation's overall security posture while optimising operational efficiency. Here are some of the key advantages.
- SIEM solutions aggregate data from diverse sources, such as firewalls, antivirus programs, and intrusion detection systems, into a centralized platform. This consolidation provides a holistic view of an organization's security landscape, making it easier to monitor, analyze, and act on security events and alerts.
- Timeliness is critical in identifying and mitigating threats. SIEM solutions monitor security events in real-time, sending instant alerts for suspicious activities. This enables swift identification and response, reducing the potential impact of security incidents.
- By correlating events across various sources and identifying abnormal patterns, SIEM solutions can more accurately detect complex threats that individual security systems might miss. Furthermore, many SIEM systems include incident response features to assist in remediation.
- For organisations subject to regulatory frameworks like HIPAA, PCI-DSS, or GDPR, SIEM solutions can aid in maintaining compliance. They collect and store logs in a secure, standardized manner, and generate detailed reports that can be invaluable during audits.
- While the initial investment in a SIEM solution can be significant, the long-term benefits often result in cost savings. By improving detection capabilities and shortening response times, organizations can mitigate threats before they escalate into more costly incidents like data breaches.
- By automating many of the time-consuming tasks related to security monitoring and compliance reporting, SIEM frees up valuable time and resources. This allows security professionals to focus on more strategic aspects of cybersecurity, such as improving defenses and educating staff.
Centralised monitoring and analysis
Real-Time Alerting
Improved incident detection and response
Compliance and Auditing
Lower Costs
Operational Efficiency
Additional content
Please take a look at our additional resources and learn more about Nomios and our SIEM expertise.
Leading SIEM technology partners
Do you want to know more about SIEM Solutions?
Our SIEM experts are here to help you. Just leave your contact information, and we will get back to you shortly.

Continue reading about SIEM

Cybersecurity
The latest cybersecurity challenges
Explore the latest cybersecurity challenges, from AI-driven threats to quantum risks, impacting organisations in an evolving threat landscape.

Usman Khan

SIEM
The essential role of SIEM in modern cybersecurity strategies
Uncover the critical role of SIEM in modern cybersecurity, featuring real-time threat detection and centralised log management for enhanced security strategies.

SIEM
8 factors you should consider before implementing SIEM
Implementing a SIEM system involves key steps like defining objectives, ensuring compatibility, calculating costs, assessing skills, ensuring compliance, evaluating infrastructure, selecting a reliable vendor, and future-proofing for cybersecurity.