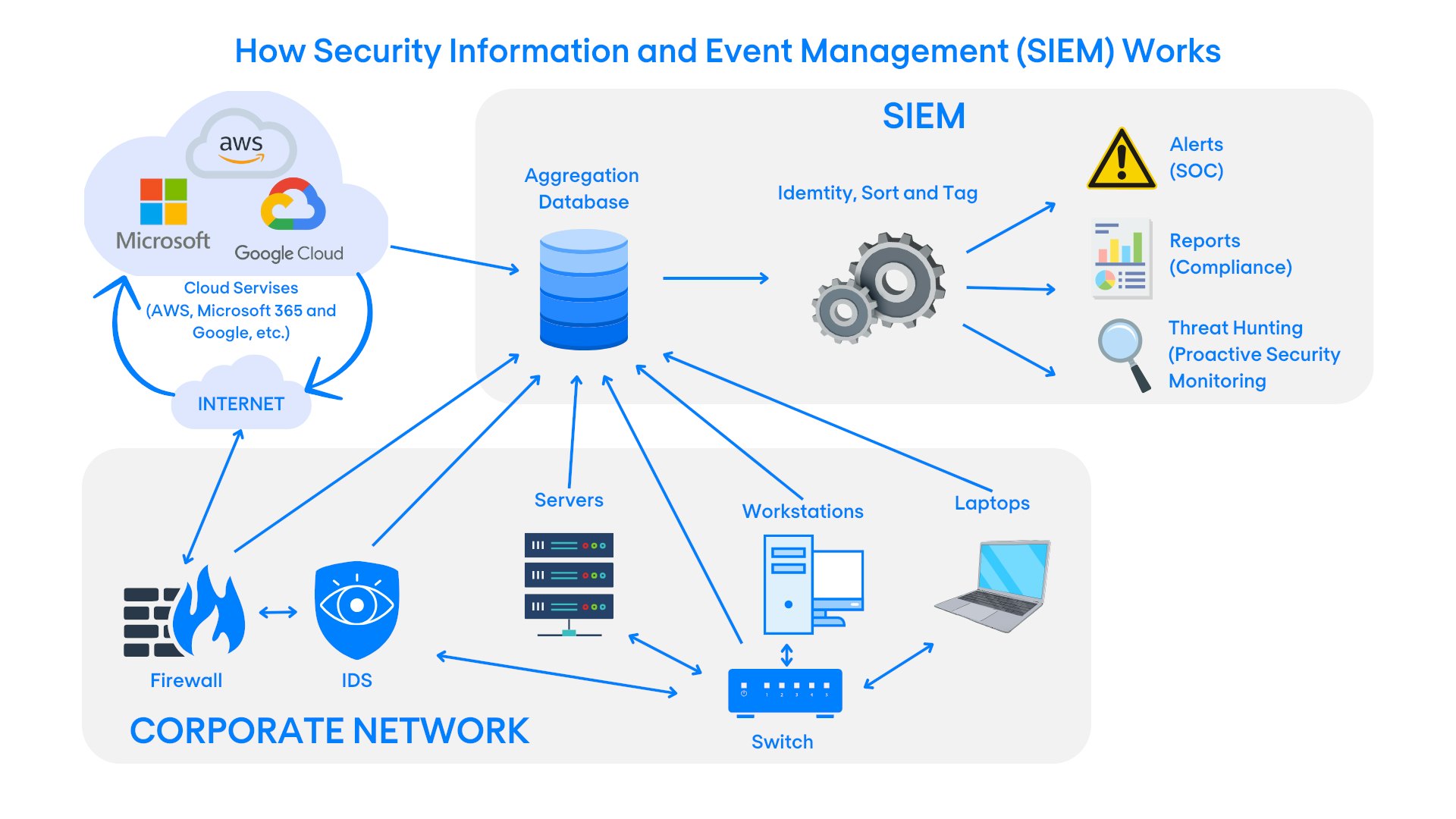
Security Information and Event Management (SIEM) systems are powerful tools that play a crucial role in modern cybersecurity strategies. They provide real-time analysis of security alerts generated by applications and network hardware, aiding in the detection, analysis, and response to security incidents. Understanding the nuances of SIEM is essential for any organisation looking to enhance its security infrastructure.
This text explores the key considerations to bear in mind when implementing a SIEM solution, ensuring you're fully prepared to integrate this complex yet indispensable system. Want to know better what a SIEM system is first? Then read our article What is SIEM?.
Eight critical considerations for selecting and implementing a SIEM system
1. Defining objectives and scope
Before embarking on the SIEM journey, it’s essential to outline your specific goals. Whether it's compliance adherence, threat detection improvement, or incident response enhancement, your objectives will dictate the SIEM system's configuration. Understanding your organisation's unique requirements is crucial for effective implementation.
2. Ensuring compatibility and seamless integration
The compatibility of your SIEM system with your existing infrastructure cannot be overstated. Its ability to integrate with different data sources and support various formats is key to efficient operation and accurate data analysis.
3. Calculating the total cost of ownership
Understanding the full cost implications of a SIEM system is vital. This includes upfront costs for software and hardware, as well as ongoing expenses like staff training, operations, and maintenance. These costs should be balanced against the potential benefits and ROI.
4. Skills and resource assessment
The complexity of SIEM systems requires specialised skills. Assess whether your team is equipped to handle these demands or if additional training and resources are necessary.
5. Adherence to data retention and compliance
Compliance with data retention laws and industry standards is a critical aspect of any SIEM system. Ensure that the system you choose can securely handle data, maintaining privacy and meeting regulatory requirements.
6. Assessing infrastructure compatibility
Your existing infrastructure's readiness for implementing a SIEM system is a key factor. The system should be compatible with various operating systems, databases, and applications, and capable of providing high availability and redundancy.
7. Meticulous vendor selection
The choice of vendor can significantly impact the success of your SIEM implementation. Look for a vendor with a strong track record, scalable solutions, and comprehensive support that aligns with your specific needs.
8. Future-proofing your SIEM System
Investing in this solution that can adapt to future technological changes and evolving security threats is essential. A scalable and flexible system will continue to serve your organisation's needs as it grows and the security landscape evolves.
Key takeaways: Making an informed SIEM choice
Selecting and implementing a SIEM system is a significant decision that impacts your organisation's overall security posture. By carefully considering these eight aspects, you can choose a solution that not only meets your current needs but also positions you to effectively tackle future security challenges.
Would you like independent advice on which SIEM product suits your organisation best, from which suppliers and how the implementation works? Then contact us.
Do you want to know more about this topic?
Our experts and sales teams are at your service. Leave your contact information and we will get back to you shortly.

Continue reading

Cybersecurity
Top cybersecurity companies to watch in 2025
We selected the top cybersecurity companies to watch in 2025, who have successfully differentiated themselves from other players in the market.

Mohamed El Haddouchi

Cybersecurity
The latest cybersecurity challenges
Explore the latest cybersecurity challenges, from AI-driven threats to quantum risks, impacting organisations in an evolving threat landscape.

Usman Khan

SIEM
The essential role of SIEM in modern cybersecurity strategies
Uncover the critical role of SIEM in modern cybersecurity, featuring real-time threat detection and centralised log management for enhanced security strategies.