As the volume and complexity of cyber attacks accelerate, Security Operations Centres (SOCs) have become the focus for bringing together the people, processes and technologies needed to defend and respond to the attacks on an organisation. However, most IT and business managers don't really know their true risk level. They have no visibility into the full range of potential vulnerabilities that could be exploited, let alone the means to fix them.
But organisations can keep abreast of modern threats by using a managed SOC. An effective SOC improves an organisation's incident detection and response capability while accelerating and improving its security posture.
Our unique managed SOC approach
Knowledge of the client's risks, its technical environment and its organisation is essential for the SOC to be able to carry out all its activities. We carry out an initial assessment of your environment to understand your organisation, your technical context, your business and the associated risks.
This insight enables us to prioritise risk coverage with you and control the "Time-To-Detect" of the serious threats to your organisation.
"A balanced approach between the newest technology and the addition of "scenarios" allows us to optimise the incident timeline by improving both detection and remediation capabilities. This is why, as part of our business and our duty to advise, we strive to remain very pragmatic about the budgetary efficiency (CAPEX/OPEX) inherent in covering your risks." - Avinash Shet, Senior SOC Analyst
Efficiency is maximised by the close proximity between the customer and Nomios. The customer has direct access to our analysts who will work hand in hand with the customer's operational security and production teams, for which Nomios is a true extension.

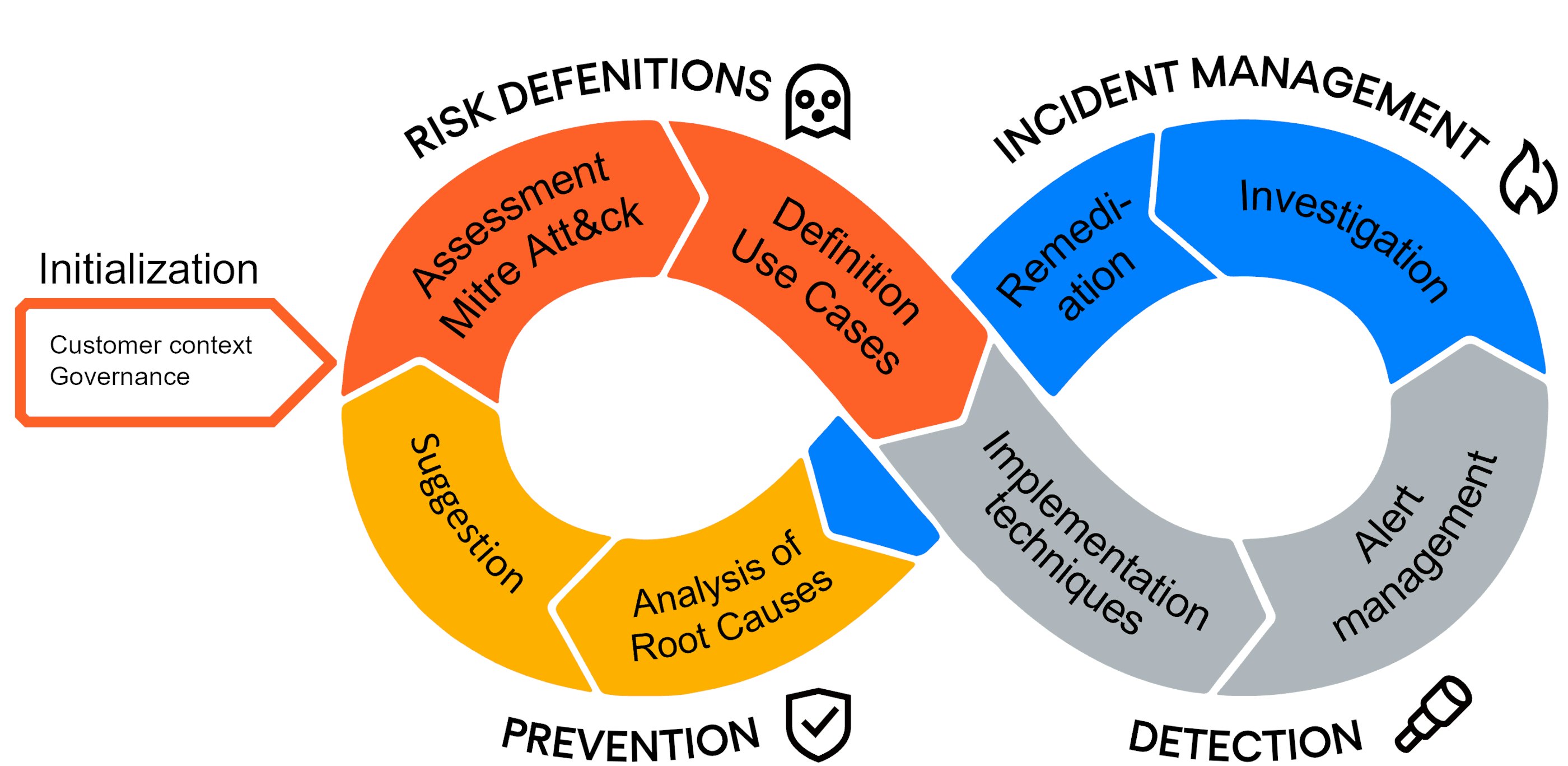
The Nomios SOC work process is agile and iterative
This agile model is the pillar of our operational security approach. It governs the quality of our offer through the iterative prioritisation of your risks, the pragmatic and total implementation of your use cases, and making the most of existing infrastructures in a continuous improvement process. The risk-based approach is the backbone of the service. We re-evaluate the risks at each iteration of the agile approach.
1. Initialisation phase
The initialisation of the service allows Nomios to get to know the technical, functional and organisational context. This discovery of your environment and your specificities is done through workshops covering your organisation and the personnel with whom the SOC will work.
This phase also allows us to frame the governance of the service with the final versions of the Service Agreement, Quality Assurance Plan and Security Assurance Plan.2. Assessment phase
Cyber risk analysis based on the Mitre Att&ck model:
- External risk assessment, based on multiple cyber threat intelligence sources. Qualification of the real risks to the organisation.
- Internal defences: analysis of your internal security situation, including policy, security tools and organisational structure.
- Consolidation: the cross-referencing of all this data will make it possible to highlight the techniques most at risk for your organisation and thus define the priorities in the actions to be taken.
3. Detection phase
This step consists of the technical implementation of the use-cases in the existing security components: SIEM/XDR, EDR, NDR and SOAR.
4. Incident management phase
After enriching the alerts (investigation, sandboxes), the correlation of indicators and the history of alerts known by the SOC makes it possible to refine the criticality of the alert to qualify it as an incident.
5. Prevention phase
Monthly analysis and consolidation of incidents in order to highlight recurring incidents. The re-evaluation of Mitre Att&ck risks and the search for root-causes allow us to propose improvement plans at each iteration of the process.
Helps reduce the complexity and cost of threat detection and incident response.
Having a dedicated managed SOC offers multiple benefits to your organisation. It's not just about detecting incidents, but also about analysing and proactively hunting down threats to help prevent attacks from happening in the first place. Discover the unique benefits of our managed SOC service.
- Security monitoring of advanced cyber threats on networks, on-premises, public cloud environments, SaaS applications and endpoints.
- Nomios SOC analysts identify and validate threats, working with your incident response team to guide, automate response and remediation.
- Detects emerging and evolving threats with continuously updated threat intelligence.
- All the benefits of a SOC while controlling the cost, complexity and time investment of an in-house operation.
- A modern security platform combines advanced qualitative tools based on machine learning algorithms, data mining tools and simulations with traditional data query and consultation approaches.
- Static security architectures are outdated and inefficient. Our adaptive security architecture is able to prevent, detect, react and predict.
Full security monitoring 24x7
Responds to threats faster
Keep an eye out for the latest threats
Controlling the SOC budget
Advanced analysis and machine learning
Adopt an adaptive security architecture
Individuals appointed for each customer and a strong team stability
Service delivery manager
This person manages the quality indicators and human resources. The service delivery manager acts as a link between the client and the technical teams in order to follow up on the various development requests.
Security engineers and analysts
Nomios has chosen to automate the actions of level 1 analysts (triage, enrichment) in order to concentrate human resources and skills on high value-added actions and not on repetitive actions that are a source of dissatisfaction for analysts, resulting in high turnover.
SOC manager
Supervises the activity of the SOC team. Manages the escalation process and reviews incident reports. Develops and executes the crisis communication plan to the CISO and other stakeholders. Performs compliance reporting and supports the audit process. Measures SOC performance metrics and communicates the value of security operations to business leaders. They also assist development teams in scoping new security development projects.

Get in touch with our security experts
Our team is available for a quick call or video meeting. Let's connect and discuss your security challenges, dive into vendor comparison reports, or talk about your upcoming IT-projects. We are here to help.