Across the market we see a clear shift towards single vendor SASE. Organisations want to simplify their IT landscape, reduce operational overhead, and gain better visibility across network and security. At the same time, large security vendors keep buying niche players to plug gaps in their portfolios. Add to that the growing attention from analysts like Gartner and Forrester, and it is no surprise that SASE consolidation dominates many discussions within security and IT teams.
The promise is attractive. One platform, one contract, one point of contact. But is a true single vendor security stack realistic for most enterprises? From where we stand, the answer is not black and white.
The limits of the single vendor promise
A single vendor SASE strategy assumes that one supplier can deliver best-in-class capabilities across secure networking, SSE, identity, threat prevention, data protection, and operations. Some vendors are getting closer through aggressive acquisitions. Still, stitching together acquired technologies into a consistent architecture takes time. Integration at roadmap level does not always mean deep integration at product level.
There is also the risk of long-term lock-in. Once core network, security, and identity are tied to one ecosystem, switching becomes harder, both technically and commercially. For some organisations, that is an acceptable trade-off. For other,s it introduces a strategic risk.
Why identity is changing the SASE conversation
The rise of identity-centric security has reshaped how SASE architectures are designed. Access decisions are no longer driven mainly by location or network segment, but by who the user is, what device they use, and what risk they bring at that moment.
This is where the combination of SSE, IAM, and secure networking starts to show real value. Instead of forcing everything into a single vendor stack, organisations can build around three strong pillars:
- SSE for cloud-delivered security controls
- IAM for identity, access, and risk context
- Secure networking for connectivity across data centre, cloud, and edge
When these layers integrate tightly, the user experience becomes smoother, security policy stays consistent, and operations become more predictable. At the same time, the organisation can still reduce the overall number of vendors and platforms.
Expertise in SSE, IAM, and secure networking
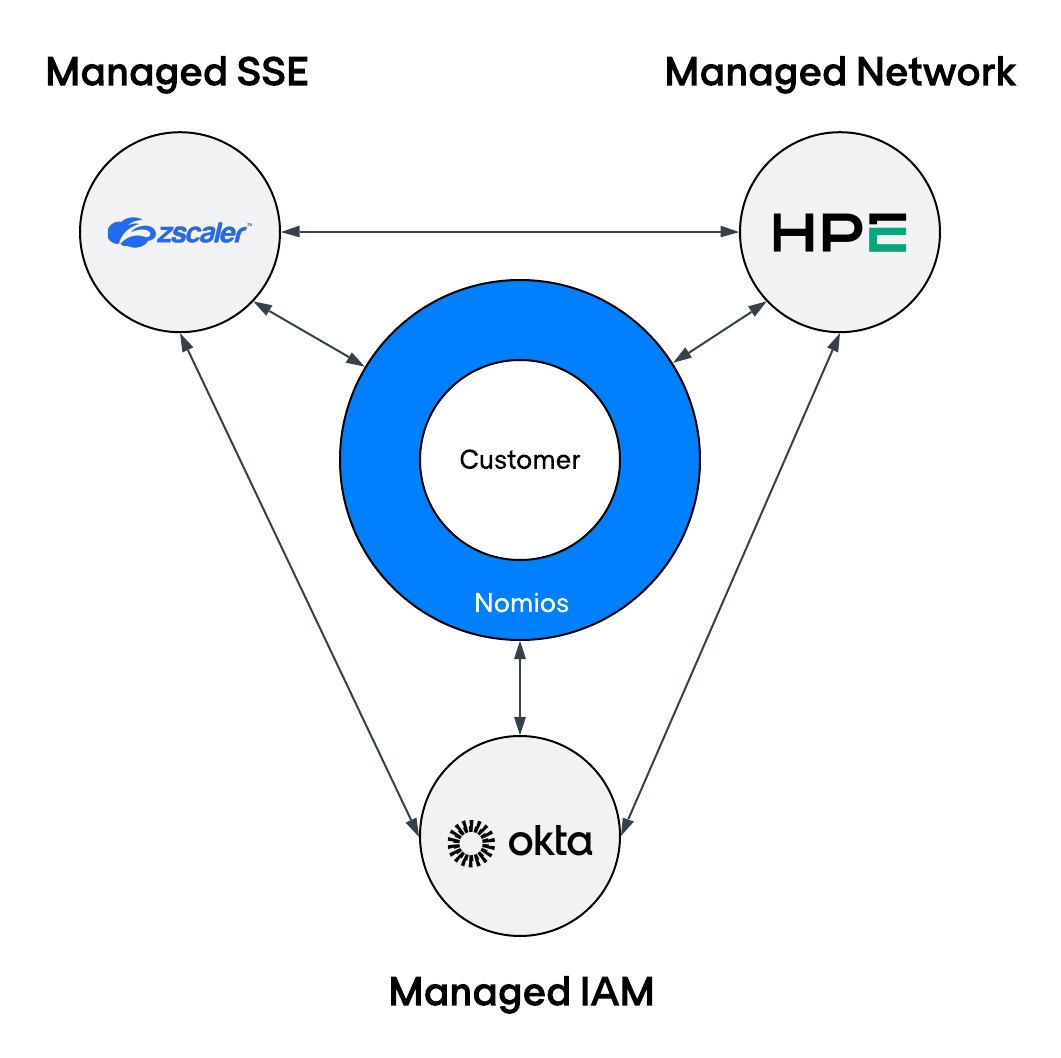
Nomios is exceptionally well-positioned to support organisations with complex challenges related to SSE, IAM, and networking. Thanks to the recent acquisition of Intragen, Nomios has further strengthened and expanded its expertise in the field of identity and access management. Intragen brings extensive experience with leading vendors such as One Identity, CyberArk, and Okta, as well as other key players in the IAM domain. This combination of deep IAM knowledge, strong SSE capabilities, and proven networking expertise enables Nomios to design and implement integrated, future-ready security architectures that align with the strategic objectives of modern organisations.
A practical best-of-breed model
A good example of this approach is a model built around:
These platforms integrate strongly at the product level. Identity informs access decisions in the security layer. The security layer ties directly into the network fabric. The result is a coherent architecture without forcing everything into a single vendor stack.
In this model, Nomios takes the role of managed security service provider. We design the architecture, integrate the platforms, and manage day-to-day operations. For many organisations, this brings the best of both worlds: fewer vendors, deep integrations, and a clear operational owner.
Single vendor or strategic partnerships?
We do not claim that one approach is always right and the other is wrong. A full single vendor SASE stack can work well in some scenarios, especially where speed and simplicity outweigh architectural flexibility.
What we do see, time and again, is that strategic partnerships across SSE, IAM, and secure networking give organisations more control over their long-term security direction. It also aligns better with how identity-driven security is being applied in real enterprise environments today.
SASE is not just a product choice. It is a strategic decision that touches networking, security, identity, and operations. Whether that leads to a single vendor or a small group of tightly integrated partners should depend on business risk, technical maturity, and long-term goals, not just on how neat the vendor's slide deck looks.
Do you want to know more about this topic?
Our experts and sales teams are at your service. Leave your contact information and we will get back to you shortly.