
Identity management
Identity security in a changing IT landscape
For a long time, identity was the neglected part of IT security. User accounts, groups and permissions were necessary to keep systems running, but rarely the subject of strategic security decisions.

Richard Landman

Zero-Trust Identity management
Why identity is the engine of zero trust
Identity is the engine of zero trust: learn how IAM, PAM and IGA enable continuous verification, reduce risk from privileged access, and strengthen identity hygiene across cloud and hybrid environments.

Mostafa Kamel


DDI
The silent weakness in higher education IT security
While universities and colleges are investing heavily in cloud, identity management and zero trust, a crucial part of the digital infrastructure remains conspicuously overlooked: DNS and DDI.

Richard Landman

SASE
Not all SASE is created equal
If you look beyond marketing terms, you will see that SASE solutions differ fundamentally in design and approach.

Richard Landman

Cloaking
App Cloaking: the invisibility cloak for sensitive applications
I first came across the term app cloaking while colleagues of mine were working on a security solution for a large international law firm. The phrase stuck with me.

Richard Landman

PKI
Why PKI is becoming a strategic pillar of modern cybersecurity
It often starts with something small. An application that suddenly becomes unavailable. An API integration that fails without a clear reason.

Richard Landman

Enterprise networking HPE
HPE Discover Barcelona 2025: Insights from the show floor
Nomios was on site at HPE Discover Barcelona 2025, joining customers, partners and HPE leaders at one of the most influential events in the networking and infrastructure calendar.

NGFW Firewall
Top 5 NGFW solutions for 2026
Explore the state of NGFW in 2026. Learn how leading next-generation firewall platforms support zero trust, hybrid cloud security, and risk reduction for modern enterprises.

Enrico Bottos

Browser
The browser as a strategic component of the security ecosystem
Over the past year, market momentum has clearly accelerated. Leading SASE and cybersecurity vendors are now explicitly positioning the browser as a core part of their platform strategies.

Richard Landman


Cryptography PKI
The plug and the key: A pragmatic view on digital sovereignty
Digital sovereignty has rapidly moved in Europe from an abstract policy concept to a concrete board-level topic. This has little to do with buzzwords and everything to do with geopolitics.

Richard Landman


Network security
Securing sensitive traffic in research networks
How research and education networks secure sensitive traffic with line-rate encryption and real-time DDoS mitigation, without impacting performance or reliability.

Michel Geensen
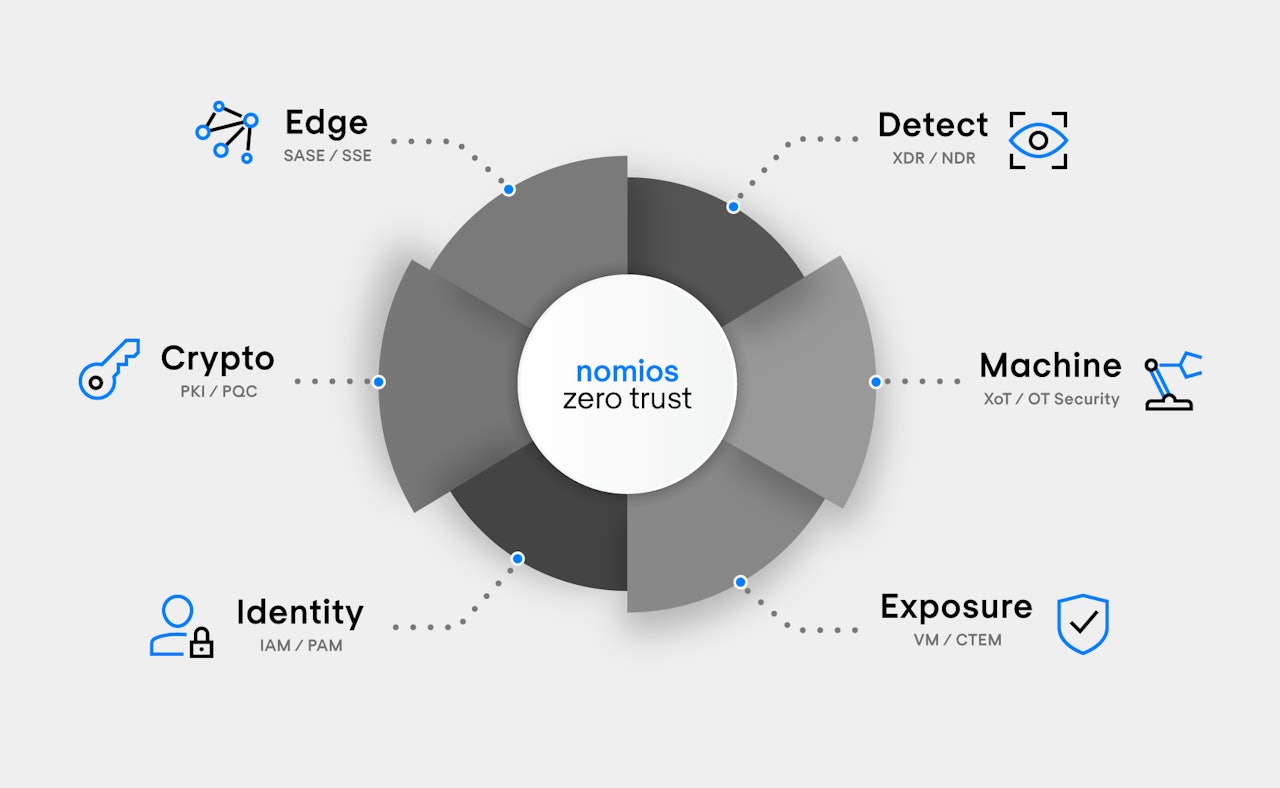
Portfolio
Nomios Zero Trust: one cybersecurity portfolio, six domains
Nomios is introducing a refreshed cybersecurity portfolio that doesn’t start with individual products, but with an architecture.

Richard Landman

Quantum Security
Understanding how post-quantum cryptography works
Post-quantum cryptography replaces vulnerable public-key algorithms with quantum-resistant designs. Learn how PQC works, which algorithm families are used, and why it runs on classical systems.

Priyanka Gahilot

Cybersecurity
Cybersecurity in 2026: Top 10 trends and challenges
Cybersecurity trends for 2026 cover digital sovereignty, quantum security, SSE and identity security, detection, compliance, and managing trust across complex environments.

Richard Landman

Quantum Security
The quantum computing threat to today’s encryption
Quantum computing threatens today’s encryption. Learn how RSA and ECC are broken, what harvest now, decrypt later means, and why organisations need to prepare now.

Priyanka Gahilot

SSE IAM SASE
Single vendor SASE? It’s all about strategic partnerships
Across the market we see a clear shift towards single vendor SASE. Organisations want to simplify their IT landscape, reduce operational overhead, and gain better visibility across network and security.

Richard Landman

Cybersecurity
Top cybersecurity companies to watch in 2026
We selected the top cybersecurity companies to watch in 2026, who have successfully differentiated themselves from other players in the market.

Mohamed El Haddouchi

Detection & Response SOC
How does AI modernise security operations?
Learn how AI enhances SecOps by reducing noise, accelerating investigations and strengthening the modern Security Operations Centre.

Nathan Oliver
Sign up for our newsletter
Get the latest security news, insights and market trends delivered to your inbox.

